Sonarqube is an open-source software quality management tool, that will analyze and measure the quality of the source code. It supports multiple languages like Java, C#, C++, Python, etc.,
It is a Java-based tool, used to perform static code analysis but it doesn’t do the logical code check. It will check for repeated code, whether we have followed design patterns or not, potential bugs, unit test cases, complex code, and syntax as well.
It will perform code coverage as well - which means how many lines of the code are tested by the unit test cases.
Hello.java – 100 lines of code
HelloTest.java – 90 lines covered, code coverage percent is 90%
Minimum project code coverage should be 80%,
To install the sonarqube the prerequisite is to have Java installed and sonarqube needs 3GB minimum so it is recommended to take a t2.medium instance at least. With this, we can do code quality checks on most of the programming languages.
The command to run sonarqube report is mvn sonar:sonar, first sonar is the plugin name and second sonar is the goal name.
We need to go to official documentation and install it, once installation is done we need to create a user called sonar and change the ownership, group permissions of the downloaded folder to sonar. We can start the sonar with the help of sonar user only, so sonar service can be started with sonar user.
Sonarqube Architecture :
Let’s say we have code in the GitHub repository, we have sonarqube scanner that will scan the code and generate the report, this report will be sent to sonarqube server. Here we have a compute engine that will categorize the report into bugs, code-smells, and vulnerabilities.
This report will be stored in sonarqube H2 Database. We can also integrate our own database as well, like PostgreSQL and MySQL which are free to use.

We can check the logs in the /opt/sonarqube/logs/sonar.log in case we come across server issues.
To generate the report we need to configure sonarqube details in the pom.xml,
We will have like this inside pom.xml.,


If we don’t want to expose our password then we can generate a token and use this token as login,

By default username and password is admin, admin. We can change it once we login to the sonarqube. If we need to give access to the developers we can create users and if they are part of sonar-users group they cannot access the Administration tab, to give admin permissions make sure you add them to the sonar-admin group.
Quality Profiles :
Quality Profile means the set of rules that we need to apply while executing the sonarqube report. If we are performing on the Java code the default one is Sonar-way, it has got around 500+ rules. We can also create our own profile and have our rules defined.
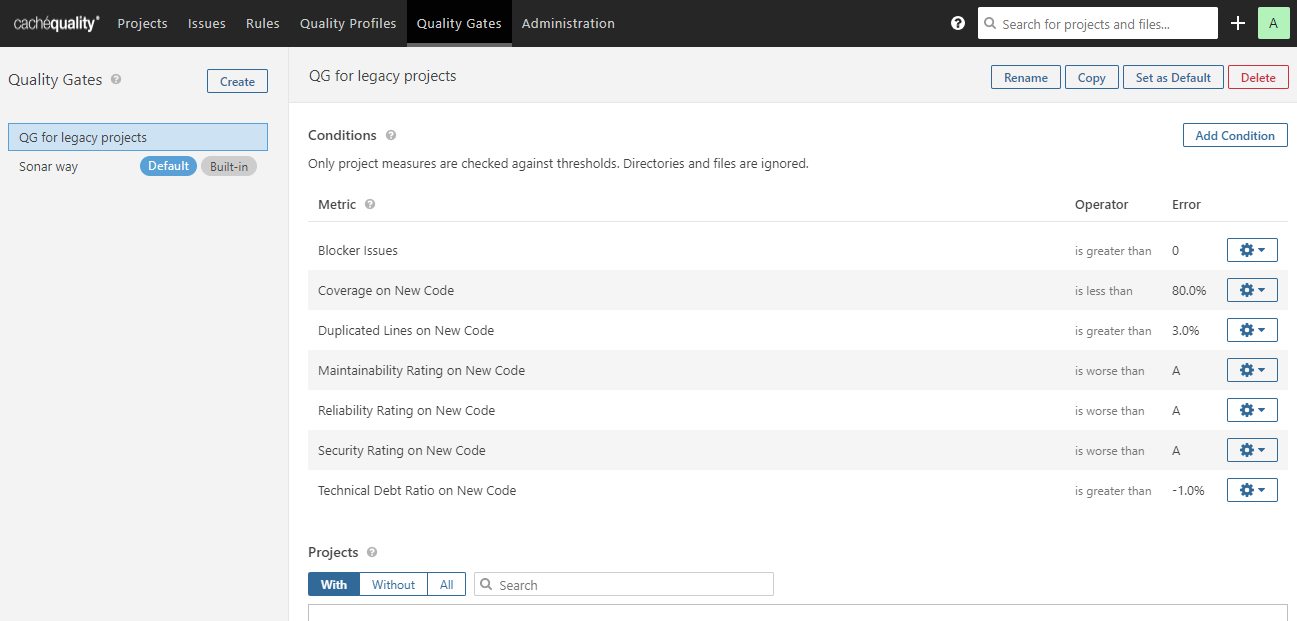
Quality Gates :
Quality Gates are a set of conditions. It will be code coverage, duplicated code, and security rating.
Sonarway is the default quality gate for Java code
We can give a condition, if code coverage is less than 80% then we can make it as failed, these kinds of conditions we can set
The homepage of Sonarqube looks like these,

We have Passed and Failed here, if it fails the conditions that we set in the quality gates then it will be marked as Failed.
